
How To Change Facebook's Default Theme To Any Color You Want
We are going to share an interesting trick on changing your Facebook default theme. You just need a Google Chrome extension to perform this trick. If you are among me who feels very fatigued with the look of Facebook's by default theme then this is a must-see post because you will find out the easiest trick to make your facebook more attractive than before.
acebook is a social networking site which empowers people to connect with friends and people around. That's how Facebook is habitually introduced. However, Facebook is beyond the need of being introduced as almost everyone is on it.
A couple of Days ago I was simply Surfing Google Chrome website and I somehow stumbled upon a Chrome Extension. Yes, a Chrome extension that will give your Facebook a Whole new look. I was apprehensive to try it, So I just installed it and checked my facebook. I was astonished to see my facebook homepage have all new look. I found it refreshing and decided to write steps on How to Change Facebook Themes using Chrome Extension.
How To Change Facebook's Default Theme To Any Color You Want
If You are among me who feels very fatigued with the look of Facebook's by default theme then this is a must-see post, Because you will find out the easiest trick to make your facebook more attractive than before. Simply follow the steps to know about it.
How to Change Facebook Theme Using Chrome Extension
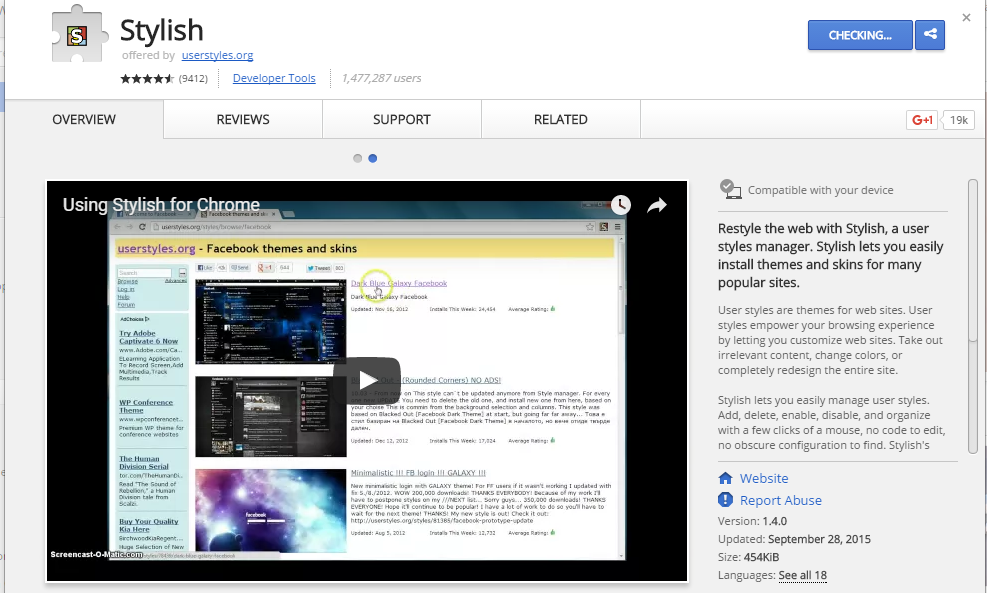
Step 1. Install Stylish for Chrome from the Chrome Web Store. It will take hardly a minute to get installed in your Chrome browser.
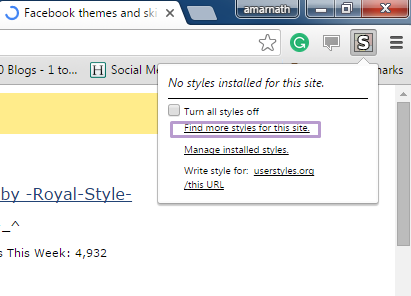
Step 2. Navigate to Facebook.com and click on the S button. Click on Find Styles for this Site to open a new tab with free themes to use for Facebook. Most of the themes are free and attractive too you can easily browse over the full website to discover your favorite theme.
Step 3. Now You will be redirected towards https://userstyles.org Guess what! This site contains huge numbers of Facebook themes, One thing is for sure that you will be confused in-between what to select and which one to skip. Select any them and click on it. Now you will be given a full preview of your selected theme.
Step 4. If everything is fine in the previewed theme, click on Install with Stylish button at the top right corner of the page. It will take few seconds or minutes depends on your theme size to be installed in Stylish Extension, once installed you will be notified with a success message.
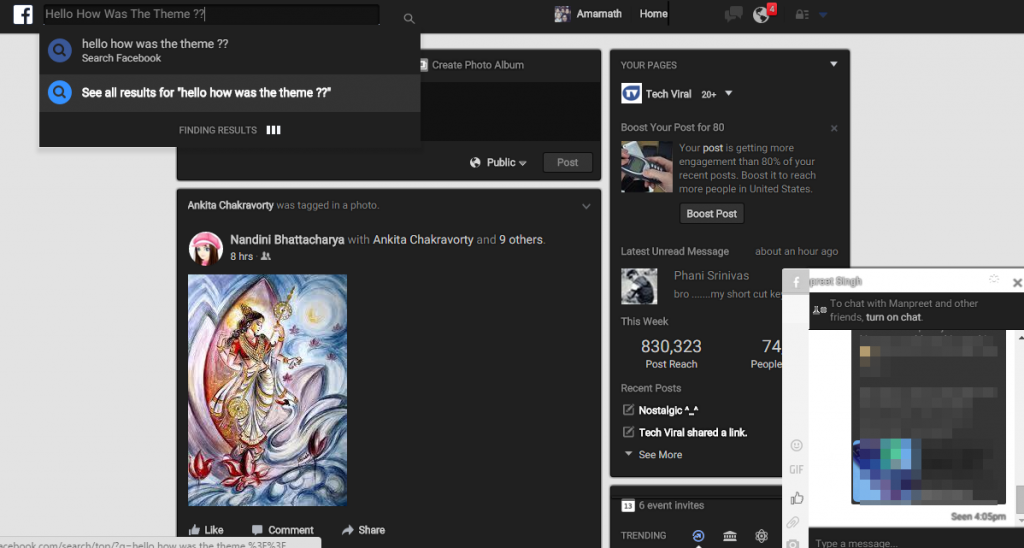
Step 5. Now whenever you open Facebook, it will show the theme that you have installed with Stylish instead of the boring old blue theme.
- Hack Website Online Tool
- Pentest Tools Url Fuzzer
- Hack Tools For Windows
- Hacker Tools Github
- Pentest Tools Online
- Hack Tools For Ubuntu
- Hacker Tools 2019
- Hacking Tools For Windows
- Hak5 Tools
- Hacking Tools Usb
- Hack Tools 2019
- Pentest Tools Linux
- Hacking Tools For Windows Free Download
- Hacking Tools For Windows Free Download
- Pentest Box Tools Download
- Hack Website Online Tool
- Hacking Tools Windows 10
- Hacking Tools And Software
- Hackrf Tools
- World No 1 Hacker Software
- Hak5 Tools
- Github Hacking Tools
- Hacker Security Tools
- Underground Hacker Sites
- Hacking Tools For Mac
- Hacker Tools Linux
- Hacker Security Tools
- Tools Used For Hacking
- Pentest Reporting Tools
- Tools Used For Hacking
- Pentest Automation Tools
- Tools Used For Hacking
- Hacking Tools Pc
- Hacker Tools Online
- Bluetooth Hacking Tools Kali
- Nsa Hacker Tools
- Hack Tools Github
- Hak5 Tools
- Hacking Tools For Windows 7
- Hacker Security Tools
- Hacker Tools For Pc
- Blackhat Hacker Tools
- Underground Hacker Sites
- Wifi Hacker Tools For Windows
- Hack App
- Beginner Hacker Tools
- Hacker Tools Hardware
- Pentest Reporting Tools
- Hacking App
- Hacker Techniques Tools And Incident Handling
- Hack Tools Mac
- Hacking Tools Kit
- Pentest Tools Windows
- Hacking Tools For Beginners
- Pentest Tools Subdomain
- New Hack Tools
- Android Hack Tools Github
- Best Pentesting Tools 2018
- Best Hacking Tools 2019
- Hack App
- Hacking Tools For Beginners
- Kik Hack Tools
- Usb Pentest Tools
- Pentest Tools Kali Linux
- Hacker Tools For Mac
- Hak5 Tools
- Hacker Tools Software
- Hack Tools Online
- Hacking Tools Usb
- Pentest Tools
- Hacking Tools For Windows 7
- Hacker Tools Apk Download
- Hack Tool Apk No Root
- Hacker Tools
- Pentest Box Tools Download
- Hacking Tools Software
- Hack Tool Apk No Root
- Computer Hacker
- Nsa Hack Tools Download
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Alternative
- New Hack Tools
- Best Hacking Tools 2019
- Android Hack Tools Github
- Hacking Tools Windows
- Pentest Tools Alternative
- How To Install Pentest Tools In Ubuntu
- Hacker Search Tools
- Hack Tools For Games
- Hacker
- Hacker Tools For Windows
- Hacker Tools List
- Hacking Tools 2019
- New Hacker Tools
- Hacking Tools For Windows
- Hacking Tools For Mac
- Pentest Tools Tcp Port Scanner
- Pentest Tools Framework
- Hacking Tools And Software
- Hacker Tools Windows
- Pentest Tools Open Source
- Hacking Tools For Beginners
- Hacking Tools Hardware
- Pentest Tools
- Hacker Tools Apk Download
- Hack Tools
- Hacker Tools
- Tools 4 Hack
- Hack Tools For Windows
- Hacking Tools Software
- Hack Tools Online
- Hacker Tools 2020
- Hacking Tools Kit
- Hack Tools Pc
- Pentest Tools Framework
- Pentest Tools Website
- Hack Tools
- Hacker Tools Windows
- Pentest Reporting Tools












.jpg)





